The Fraud Arms Race: Why Your 2023 Vetting Process is Obsolete in 2026
Freight fraud has evolved into an enterprise-level industry using AI and synthetic identities, rendering 2023 vetting protocols obsolete. To prevent theft, brokers must shift from compliance to counter-intelligence: use "Pattern of Life" analysis to detect behavioral anomalies and mandate real-time driver tracking. Verify the physics, not just the paperwork.
Nov 14, 2025
Omar Draz • Co-Founder
Freight fraud has shifted from a crime of opportunity to a capital-intensive industry. In 2026, you are not fighting a lone scammer with a fake Gmail account; you are fighting enterprise-level syndicates with R&D budgets.
Many brokerages operate on a 2023 security model designed to catch messy, low-effort scams. That model is obsolete. The modern fraudster operates like a CEO, calculating ROI and investing in technology that bypasses standard compliance checks.
If you treat fraud prevention as a checklist rather than a counter-intelligence operation, you will lose. Here is the economic and technical reality of the current threat landscape.
The Compliance Gap: Why "Good Enough" is Now Dangerous
The standard vetting process used by the majority of brokerages—checking the FMCSA website and calling the phone number on file—is no longer a security measure. It is a terrifying vulnerability.
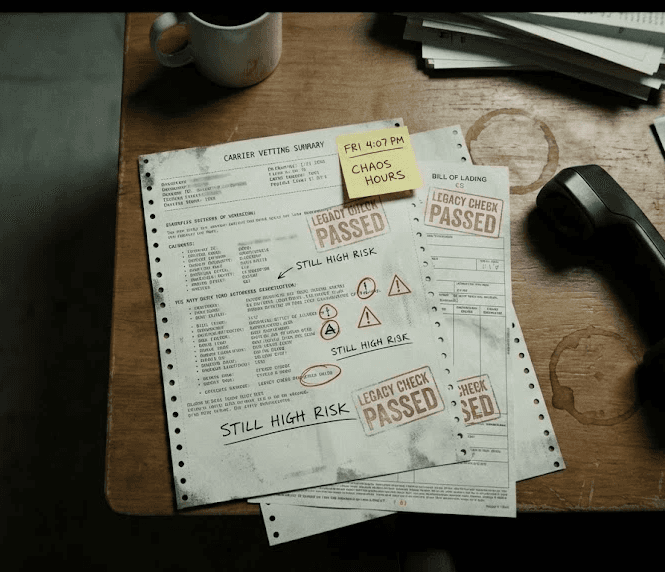
The "Speed vs. Security" Trap
Fraudsters understand your dispatch floor better than you do. They know that at 4:00 PM on a Friday, vetting protocols compress. When a customer demands coverage for a dropped load, the pressure to "get it covered" overrides the instinct to verify. Syndicates specifically target these "chaos hours," betting that your desire for revenue will outweigh your fear of loss.
The "Legacy Vetting" Problem
For twenty years, a valid MC number and a matching phone number were the gold standard of verification. Today, that is the bare minimum. A fraudster can buy a clean, aged MC number on the black market, update the phone number in the FMCSA database to a burner phone they control, and pass your "legacy" vetting in five minutes. If you rely on the government database as your primary source of truth, you are validating the criminal, not the carrier.
The False Sense of Security
Many brokers believe their TMS (Transportation Management System) acts as a firewall. It does not. Most onboarding software checks static data: Is the authority active? Is the insurance valid? It fails to check dynamic behavior: Is the person on the phone actually in the United States? Is the dispatcher's voice consistent with the carrier's history? A green light in your TMS often just means the paperwork is clean, not that the truck is real.
The ROI of Theft: View the Fraudster as a CEO
To stop the fraud, you must understand the business model. Cargo theft is no longer about desperation; it is about yield. Syndicates invest in fraud because the Return on Investment (ROI) beats legitimate logistics.
The "Criminal P&L" Statement
Consider the economics of a single strategic theft operation. The barrier to entry is financial, not physical.
Cost of Goods Sold (COGS):
Clean, aged MC Number (Black Market): ~$5,000
AI Voice Cloning Subscription: ~$50/month
Fake Domain & Email Setup: ~$20
Total Investment: ~$5,070
Revenue:
One truckload of copper or high-end electronics: $100,000+
Net Profit: ~$94,930 per load.
The Scalability Factor
Because the margins are this high, criminal organizations are scaling. They are not pocketing the cash; they are reinvesting profits into better technology and "staff." We now see fraud rings with shifts of workers operating 9-5, whose sole job is to impersonate dispatchers and book loads.
Risk Arbitrage
Compare this to physical bank robbery. Robbing a bank carries extreme physical risk and federal prison time for a relatively low take (often under $10,000). Digital freight fraud carries near-zero physical risk—the perpetrators are often overseas—and the financial reward is 10x higher.
The New Battlefield: Identity is the Asset
The modern fraudster does not break locks; they break information chains. They are investing heavily in Identity Theft and Synthetic Identity creation.
Synthetic Identities Syndicates are no longer just stealing existing identities; they are manufacturing new ones. They will register a carrier authority, pay the insurance premiums, and let it sit dormant for 6 to 12 months. This "aging" process allows the carrier to bypass your "New Entrant" flags. They may even run legitimate loads for months to build a credit history before conducting a "bust-out" scheme, stealing multiple loads in a single weekend.
Deepfakes & AI Voice Cloning
This is the most significant technical escalation in 2026. Security protocols often rely on a phone call to "feel out" the dispatcher. This is now a liability.
Fraudsters record legitimate dispatchers.
They feed as little as three seconds of audio into AI cloning tools.
They use text-to-speech software to speak to you in that stolen voice in real-time.
When a robot sounds exactly like a tired dispatcher from Texas, "gut instinct" becomes worthless.
The "Digital Heist"
The theft occurs in the email server, not the loading dock. Syndicates use phishing to gain access to a legitimate carrier's email. They intercept Rate Confirmations, change the pickup instructions, and vanish. The driver who shows up is real, the broker is real, but the communication bridge was hijacked.
Counter-Measures: How to Outspend and Outsmart
You cannot out-work a computer, but you can out-process a criminal. You must move your defense budget from "Verification" to "Visibility."
Invest in "Pattern of Life" Analysis Stop looking at the carrier's paperwork and start looking at their physics.
Inspection Logic: Does a carrier with one truck have a roadside inspection in California and Florida on the same day? That is physically impossible and indicates a double-brokering scheme.
Address Validation: Did their office address recently change from a commercial trucking yard to a residential apartment or a virtual office in Delaware?
Driver Visibility is Non-Negotiable The only truth in logistics is the physical location of the driver’s phone.
No Tracking, No Load: Stop accepting "check calls." Require real-time tracking via tools that ping the driver's actual cellular device.
Bypass the Dispatcher: If a dispatcher refuses to provide the driver's direct line for tracking setup, refuse the load.
Conclusion: It’s an Arms Race, Do Not Disarm
Freight fraud is an evolutionary arms race. As brokers build higher walls, fraudsters build taller ladders.
Schedule a Demo of Indemni’s visual verification system and see how easily it integrates with your existing operations.

